How EnableViewStateMAC Makes ViewState Secure
How EnableViewStateMAC Makes ViewState Secure ?
__VIEWSTATE. Typically, stored ViewState information looks like:
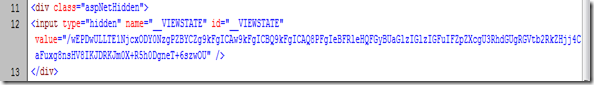
ViewState value looks likes an encrypted string. This is nothing but a Base64 encoded string, and is not an encrypted string. So it can be easily decoded.
The main reasons for using Base64 encoding are as follows:
- Base64 makes a string suitable for HTTP transfers
- It makes it a little harder to read
Let us try to decode the string using ViewState Decoder (a nice tool created by Fritz Onion).
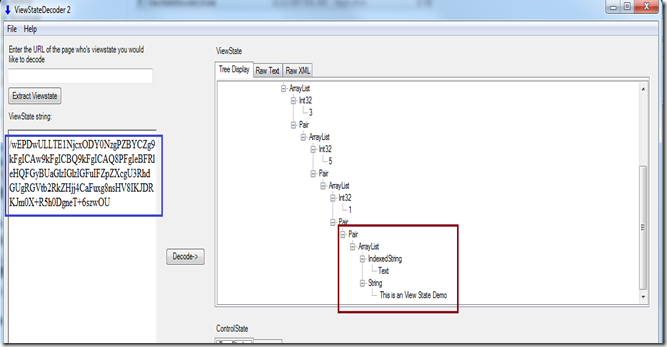
After decoding the string, we can see the exact data that is stored inside the ViewState.
You can write a few lines of code to decode the text and you will get the actual View State information.
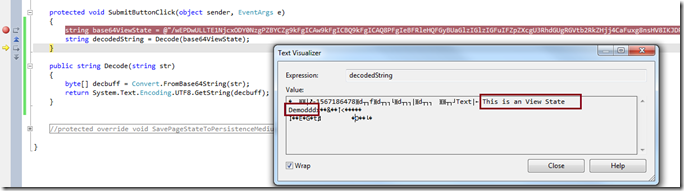
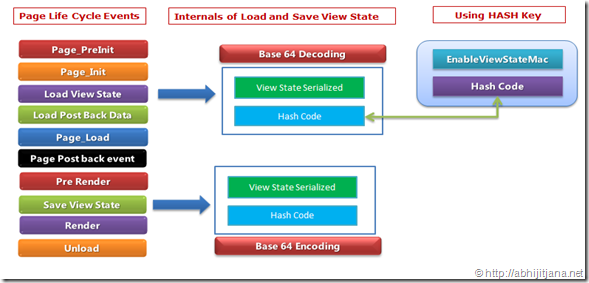
By default, ViewState is serialized into a Base-64 encoded string. On postback, the ViewState information is loaded and reapplied to the persisted state of the control in the control hierarchy.
You can make sure that the ViewState information is tamper-proof by using “hash codes”. You can do this by adding
EnableViewStateMAC=true in your page directive. MAC stands for “Message Authentication Code”.
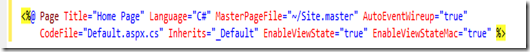
When we use
EnableViewStateMac="True", during
ViewState save, ASP.NET internally uses a hash code. This hash code is a
cryptographically strong checksum. This is added with the ViewState
content and stored in a hidden filed. During postback, the checksum data
is verified again by ASP.NET. If there is a mismatch, the postback will
be rejected.
Sagar S Bhanushali
Comments
Post a Comment